Mitigating MAC flooding attacks using port security techniques
Keywords:
MAC Flooding Attacks, Port Security, Local Area Network, MAC address limiting, Packet tracerAbstract
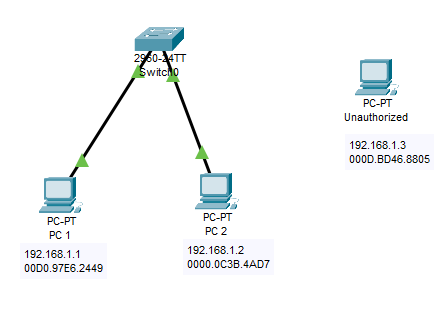
In today's interconnected digital landscape, network security is paramount, particularly for Local Area Networks (LANs) that are increasingly vulnerable to MAC flooding attacks. These attacks exploit vulnerabilities in network switches, compromising network integrity and privacy. This study aims to explore the effectiveness of port security mechanisms in mitigating MAC flooding threats through a practical simulation using Packet Tracer. The simulation setup includes a switch, two authorized computers, and one unauthorized computer, with a strict limit of one MAC address allowed per port. Shutdown violation is set whenever the switch port learn more than 1 MAC address to avoid MAC flooding. The findings reveal that the implementation of MAC address limiting effectively prevents the learning of additional MAC addresses, thereby safeguarding the network from potential flooding attacks. When the maximum MAC address limit is reached, the port is shutdown as set in the violation mode. This research underscores the critical importance of proactive security measures in maintaining network integrity and provides valuable insights for network administrators seeking to enhance their security protocols.
Published
How to Cite
Issue
Section
Copyright (c) 2025 Shehu Ibrahim Gajo (Author)

This work is licensed under a Creative Commons Attribution 4.0 International License.




